There is never a ‘good’ time to suffer a cyberattack, but for Life Healthcare Group it could not have come at a worse moment. In the midst of the worldwide COVID-19 outbreak, with healthcare workers already battling to contain the crisis, SA’s second-largest private-hospital operator was forced to take its systems offline.
‘We are deeply disappointed and saddened that criminals would attack our facilities during such a time, when we are all working tirelessly and collectively to fight the COVID-19 pandemic,’ said Pieter van der Westhuizen, acting group CEO. His frustration was obvious – and understandable. There, in the middle of an unprecedented health crisis, the JSE-listed group was forced to switch its hospitals and administrative offices over to ‘backup manual processing systems and continue to function, albeit and regrettably, with some administrative delays’.
The WHO had a similar experience, with a ‘dramatic increase in the number of cyberattacks directed at its staff and email scams targeting the public at large’. In late April, 450 active WHO email addresses and passwords were leaked online, along with thousands belonging to other individuals working on the coronavirus response. The organisation confirmed that the number of cyberattacks it experienced in April 2020 was more than five times the number it faced during the same period in 2019.
Those incidents were inevitable. A report released in April by New York Stock Exchange-listed professional services company Accenture confirmed that the cyberattack surface had grown tremendously in the previous year, with threat actors targeting SA entities on all fronts.
‘Our research found that approximately R2.2 billion a year is lost to cyberattacks,’ according to Clive Brindley, senior manager within the security practice at Accenture in Africa, adding that SA’s cross-industry spike in cyberattacks in 2019 made it the country with the third-highest number of cybercrime victims worldwide. He attributes the increased focus on SA to a variety of interconnected factors, including lack of investment in cyber-security, developing cybercrime legislation and law-enforcement training, and poor public knowledge of cyberthreats.
‘Many developing economies consider cybersecurity a necessity but are not capable of investing sufficient funds as they battle to fight other social problems such as high crime rates, inequality and poverty, as well as high unemployment, and a shortage of skilled labour,’ he says.
Take that environment, and then – at a few days’ notice – force the vast majority of your workforce to work from home, and you get the perfect cyberthreat storm that hit SA during the COVID-19 crisis.
Mimecast’s 100 Days of Coronavirus report found that cybercrime surged by 33% in Q1 2020, and warned that ‘threat actors and criminals will almost certainly (>95%) seek to exploit the increased numbers of employees working from home and see them as an enhanced opportunity to compromise secure workplace networks’.
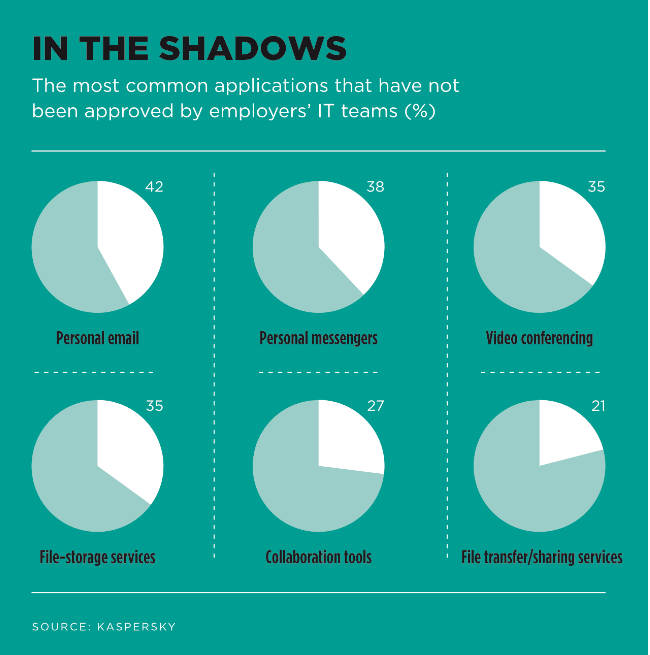
They’re right, of course – and a survey by digital security firm Kaspersky suggests why. In mid-May, it released a global report, which found that 73% of employees working from home (WFH) had not received any specific cybersecurity awareness guidance or training. More than a quarter of the WFH employees surveyed added that they had received phishing emails on the topic of COVID-19, while – and here’s the really scary part – many admitted that they’d also increased the use of online services that weren’t approved by their IT departments. These included video conferencing, instant messengers and file-storage services.
You or your employees are probably guilty of this yourselves, whether it was a quick Zoom call with friends or clients, a WhatsApp group for your team, or a Google Drive folder for sharing documents. And, as Kaspersky points out, while employees were adjusting to WFH, it was important for businesses to ensure those employees could work as they usually would.
‘It is hard to keep things “business as usual” when everything needs to change so dramatically,’ says Andrey Dankevich, Kaspersky senior product marketing manager. ‘While employees are trying to get along with the new reality of working from home, IT and cybersecurity teams are under pressure to enable them to continue working safely.
‘Cyber incidents can only add difficulties to this challenge, so it is important to remain vigilant and make sure remote working is also secure working.’
A closer look at the Kaspersky report reveals just how blurred the lines became between W and H. Some 42% of surveyed workers said they were using personal email accounts for work, and 49% admitted to increasing how often they do this. Then, 38% said they were using personal messengers for professional reasons, with 60% saying they were doing this more often since they started working from home. And, in news that will have had IT departments worldwide weeping into their coffee, some 51% of workers admitted to watching adult content on the devices they use for work purposes.
The stats are even more alarming for small businesses. Kaspersky found that 57% of employees of small organisations were not provided with corporate devices from their employers during the pandemic, and just 34% of small-business staff reported being given IT security requirements to work securely on their personal devices. ‘Small companies may be in difficult circumstances, and their first priority is to save their business and employees during the lockdown. So it’s no surprise that cybersecurity may become an afterthought,’ says Dankevich. ‘However, implementing even basic IT security requirements can decrease the chances of malware infection, compromised payments or lost business data.’
The dramatic increase in remote working brought with it a rise in the use of video-conferencing platforms such as Zoom, Skype, and Microsoft Teams – with Zoom, especially, coming under fire for the holes in its security. ‘Where users go, malicious actors soon follow,’ Kiri Addison, Mimecast’s head of data science for threat intelligence and overwatch, notes in an early April online post.
‘We’ve seen an increase in threats seeking to exploit the popularity of the most widely used and trusted video conferencing platforms by creating phishing campaigns and fake websites. In addition, the fact that information for many video conferences is publicly available has facilitated the growth of so-called “Zoom-bombing”, in which unauthorised users attempt to disrupt or take over online meetings. These platforms are now responding with updated security features and best practices, but users should still exercise caution.’

Mimecast estimates that in early April, 10% to 15% of all email spam was COVID-related (this after spikes of up to 18% to 20% in late February). As an expert panel points out in a Mimecast webinar, the decrease in COVID-related spam was due to the global workforce becoming more savvy about being cyber-resilient at home. But, the panel notes, when spam and opportunistic attacks stop working, attacks become more sophisticated.
Right on cue, impersonation attacks increased by 30.3%. In these particularly nasty cyberattacks, cybercriminals mimic internal company notices – for example, a letter from the CEO regarding a post-lockdown return to office work – to lure unsuspecting victims.
So what’s next? ‘The dust is still settling. But some major themes are emerging,’ says David Ferbrache, global head of cyber futures at KPMG in the UK. ‘Enterprises will have to evolve, working to improve their supply chain resilience, adapt to geopolitical challenges and tensions impacting the global market, and adjust to new labour-force models and working practices. They’ll have to do all of that in the face of a seismic shock to the global economy and, for many sectors, ongoing liquidity and debt challenges.’
Ferbrache adds that ‘in the wider ecosystem, the pandemic has outlined the need for greater co-operation and collaboration across both public and private domains as we all tackle the challenges of COVID-19, including ruthless entrepreneurial cybercriminals who exploit the situation for gain’.
There is, of course, plenty that companies can do to improve cyber defences, even (or especially) while some employees are still working from home. Kaspersky recommends ensuring employees have all they need to securely work from home and know who to contact if they face an IT or security issue, while Mimecast advises updating your enterprise email security protections (here they point to a recent report that only 60% of organisations ‘have some kind of security system to protect their data or employees in internal and outbound emails’).
People (in other words, employees) tend to be every organisation’s weakest point when it comes to cybersecurity. But an employee’s laptop antivirus software shouldn’t be the only line of defence. As Mimecast points out, ‘any important business process that can be disrupted or taken advantage of via a single point of failure, is not sufficiently resilient’. Ultimately, as with COVID-19, cyber protection comes down to common sense, caution and good hygiene.








