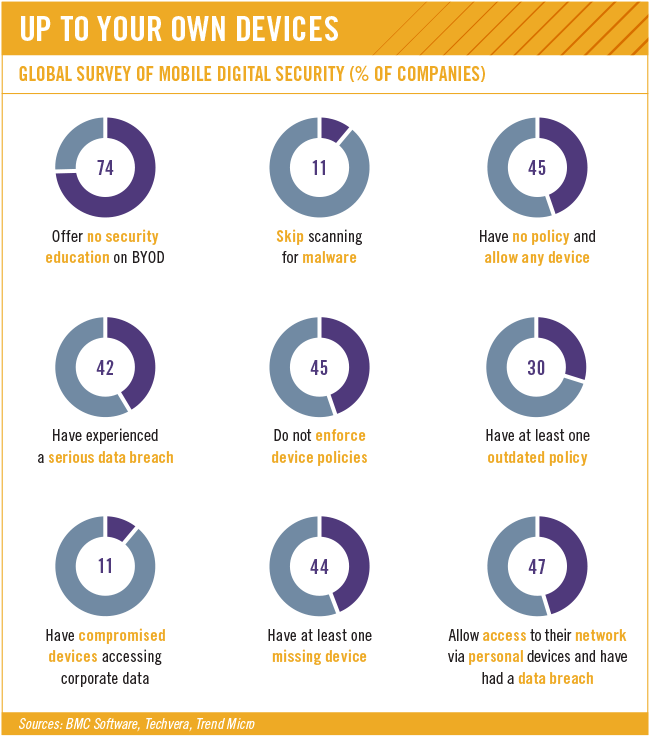
Any modern business fears the unauthorised access to or theft of its confidential data. The trend for business to adopt a digital, mobile and/or bring your own device (BYOD) strategy at the workplace is rapidly intensifying this concern. Should a company experience a breach, the legal ramifications are serious and can be enormously damaging.
‘Allowing such fear to debilitate progress in the business by not adapting to digital and mobile technology can have even more significant and harshly felt effects on the business,’ says Alessandro Postiglioni, head of IT security at BT in Africa. ‘It’s about striking the right balance between meeting demand for mobility within the enterprise, while still protecting the business’ core data assets.’
Postiglioni adds that it used to be much simpler for businesses to protect devices at work but today, rapid advances in and adoption of mobile working and the BYOD trend has not only added layers of complexity to protecting the business and devices at work, it has also made endpoint security more critical than ever before.
Ruckus Networks sub-Saharan Africa sales director Riaan Graham states that the main risk of BYOD is that the core infrastructure of an organisation may not be capable of properly on-boarding and securing that device onto the network, which leaves the company open to security concerns. ‘A company needs to clearly understand what the strengths of its security in the core of the network are, rather than try to limit the type of devices that get used,’ he says. ‘It’s very difficult to control external devices coming into your environment. It’s easier to control your security parameters in the network.’
Denis Legezo, antivirus expert at Kaspersky Lab, notes that while a company is responsible for internal devices such as PCs and networks, it is similarly responsible for any devices that could lead to a breach of the company’s security perimeter. Smartphones, for instance, function within this perimeter at the office as well as outside of it, such as when they are taken home with employees, he says. ‘This means they could be connected to rogue hotspots or that applications could be installed outside the security perimeter.’
Legezo suggests that corporates use sandboxing or secure virtual private networks on devices. This essentially means that all applications related to the company will be kept in a standalone environment on the device, with the user’s own apps outside of this. Such segregation of information enables remote wiping of lost or stolen devices, or in situations where an employee leaves the organisation.
He also notes that companies should encrypt any devices – supplied to the employee – which leave the premises each day, and ensure that they have adequate corporate security policies in place (backed up by training) governing how employees use such devices. ‘By taking these steps you can mitigate threats coming from such devices.’
According to Postiglioni, enterprise mobility management (EMM) solutions can help businesses extend their mobile working in a secure way, through set controls that can reduce mobile costs and maintain corporate security. He explains that ‘EMM solutions enable businesses to manage, monitor, secure and support mobile devices as their employees connect to the business’s internal networks and systems. The solution also provides fail-safes where the business’s IT teams can remotely disable or bar devices in the event of loss or theft, as well as ensuring that corporate data and security isn’t compromised by staff accessing systems on different devices’. EMM solutions are designed and equipped to deal with issues around apps that employees download, and that are inappropriate for their corporate device, he adds.
When deploying a digital strategy, Postiglioni says businesses need to adapt a far more proactive approach to security. With the advent of cloud computing and the mobile digital workforce, business security controls must protect all employees – as well as the sensitive data that they access – across a plethora of locations, devices and content types, he comments. ‘Some businesses approach this challenge by loading security software onto every device. While this is a manageable strategy, a device-centric approach to endpoint protection can be costly, administratively intensive to implement and resource-intensive to maintain – especially if you consider how quickly new devices or app updates are launched.’
That said, embracing the capabilities that come with new and innovative technologies, including cloud computing and the internet of things, businesses can build more effective prevention capabilities across the exploding number of endpoints, according to Postiglioni.
Graham comments that an organisation needs to be confident that its core network has been built up, and is secured robustly enough for access from any typical device. ‘If you’re going to try secure every device, you’ll have endless nightmares. Rather look at your core infrastructure to ensure it is as bulletproof as possible. Work from the inside out.’
When putting together a BYOD policy, Wilmari Strachan, director in ENSafrica’s technology, media and telecoms department, suggests that companies ensure it includes acceptable use guidelines; security and access controls; limited or no access to certain websites through the company network; clear guidance on what devices may or may not be used in the workplace; procedures to follow in the event of a security breach; password policy; the company’s rights relating to employees’ own devices; and ownership of data or company intellectual property. ‘The BYOD policy is intended to protect the security and integrity of the company’s data and technology infrastructure by providing guidelines, rules and sanctions for non-compliance,’ she says.
Likonelo Magagula, director for intellectual property at Norton Rose Fulbright, adds that another crucial aspect of a successful BYOD policy is implementing adequate education and training of all employees on how to mitigate against IT and security risks as well as respond to security incidents.
As for compiling a BYOD policy, Magagula says there is no hard and fast rule as BYOD policies vary depending on the industry the company operates in, the information processed by the personal devices, and the compliance requirements to which the company is subject. ‘It is prudent for organisations seeking to mitigate IT risk – in a legal sense – to conduct a due diligence on their current system to ensure the scope of the existing software agreements and licences is sufficiently broad to cover the breadth of the BYOD policy they intend to implement.’
A key legal consideration of a BYOD policy includes the Protection of Personal Information Act (POPI), along with other laws and legal doctrines, adds Magagula, which might place obligations on certain organisations to put measures in place to ensure the security of data. With regards to the legal ramifications should a company experience a breach in security through a device, Magagula says that non-compliance with POPI may result in a civil, enforcement or criminal action for any offence committed. ‘Convictions may give rise to imprisonment, a fine or both imprisonment and a fine depending on the circumstances.’
Asked what liability the employee has in the event of a breach, Magagula explains this will depend on several factors, including whether the employee acknowledged responsibility and was trained how to identify security threats and the appropriate way to respond to security incidents. ‘Their liability will depend on the policy created, the relevant applicable laws and the circumstances surrounding each individual case. All in all, the most important protection for a company would be cyber-liability insurance and placing adequate security controls to effectively protect privacy,’ she says.
According to Strachan: ‘If the employee acted reasonably and in accordance with the company’s policy, he/she would not be liable. However, if the employee acted contrary to or in breach of the company’s BYOD policy, then the sanctions set out in the policy would follow. If the company had no BYOD – or similar – policy governing the use of own devices, it would have to consider whether the employee acted reasonably or in breach of his/her contract with the company.’
Postiglioni believes that enterprise mobility and the BYOD trend will continue to experience remarkable market acceleration in the coming years. Thus, businesses need to be proactive. ‘Businesses can no longer afford to treat security as an isolated silo – it’s beyond just putting up fences. Rather, business must take initiative and start being more proactive about managing their security as a central facet to delivering on the strategic goals of the company.’